“Title inspired by Iron Maiden”
It happens every now and then – you are looking for something on your file shares and notice one file that just doesn’t seem to fit in. They are usually executable files with rather obscure names (e.g. qZrkrf.exe) and have most certainly no business being on your servers. You realize that once again a worm made it into your environment and your trusted antivirus solution is not recognizing this variant yet – great.
This is probably a familiar scenario for most IT/Security teams and doesn’t cause too much of a headache. Still it would be nice to be a bit ahead of the curve and have some way to get an early warning without deploying complicated technology. One option that you might not think of right away is leveraging Windows file screening functionality. Introduced in Windows 2003 R2 it provides a simple way to prevent users from storing certain file types on your shares… purposely or inadvertently. Jose Barreto provides a brilliant guide showing how to install and configure file screening so i’ll keep the technical details brief.
For this purpose we are only interested in potentially malicious content. Windows already provides a file group that includes executable file types which is what we are looking for.
Even more convenient there already is a template we can use.
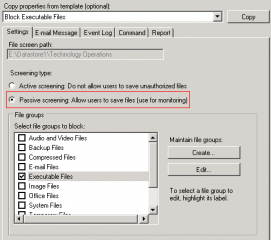
Really all we need to do is to select ‘ Create File Screen’ in the action panel and choose the ‘Block Executable files’ in the configuration section. This can be applied to the root of the share or any subdirectory. Keep in mind however that you can only directly apply one file screen per directory. Higher level screens will be inherited by lower level directories however.
Once it is applied the server will no longer allow any of the file types listed in the group to be written to the directory and present an ‘Access denied’ error. This is quite useful but probably won’t fly in most environments as it restricts the user considerably.
Fine, we can’t prevent the potentially malicious file from being stored on the share but we can at least make sure we know about it and raise a red flag that something is going on! All we need to do is to modify the properties of the file screen and select passive mode.
Assuming that the SMTP settings were configured (File Server Resource Manager/Configure Options) and the file screen is set up with an email address to reach the administrator no executable file should find its way onto your server undetected going forward. As you can see from the picture below the notification also shows the user account which is writing the file to the share making it very easy to contact or cut off the culprit.
In most environments users are not supposed to store executable files on a regular basis so the noise should be fairly low. The next time a worm goes undetected by your antivirus solution you will know about it pretty quickly as the notification messages pile up in your inbox. And all it cost was a couple minutes configuration which can even be automated.